What is yy68kzj?
In the ever-expanding digital universe of codes, alphanumeric sequences, and cryptic identifiers, “yy68kzj” stands out—not because it’s widely known, but precisely because it isn’t. In an online world dominated by trending topics, algorithms, and hashtags, the obscure keyword yy68kzj is gaining traction among early adopters, tech bloggers, and curious data miners alike. But what exactly is yy68kzj, and why is it starting to pop up in conversations around digital culture, data organization, and cryptographic experimentation?
At its core, yy68kzj represents a seven-character alphanumeric sequence that blends letters and numbers in a seemingly random pattern. Unlike traditional keywords or branded identifiers, this code doesn’t immediately reveal its purpose or origin. It exists in a gray space between technical jargon and digital mystery, making it fascinating for those who appreciate the hidden layers of the internet.
The sequence follows a specific structure: two lowercase letters, followed by two digits, and concluded with three lowercase letters. This composition isn’t arbitrary—it suggests intentional design rather than random generation. Whether it serves as a product code, database key, or experimental identifier remains part of its allure.
The Origin Story: Where Did yy68kzj Come From?

Tracing the roots of yy68kzj proves challenging, as the code doesn’t appear in mainstream databases or popular platforms. Some digital archaeologists speculate that it emerged from beta testing environments, where developers often use non-obvious identifiers to track projects without attracting unwanted attention. Others believe yy68kzj originated within closed communities focused on data science or cryptographic hobbies.
What makes the origin story compelling is the lack of a definitive answer. Unlike corporate product codes that come with press releases and marketing campaigns, yy68kzj appears to have grown organically through word-of-mouth and niche forum discussions. Early references suggest it may have first surfaced in technical documentation or as part of an internal tracking system that later leaked into public consciousness.
The anonymity surrounding its creation adds to the mystique. Without a clear creator or company claiming ownership, yy68kzj exists as a kind of digital artifact—owned by no one and potentially useful to everyone. This democratic nature makes it particularly appealing for independent developers and creative technologists looking for unique identifiers.
Decoding yy68kzj: A Structural Analysis
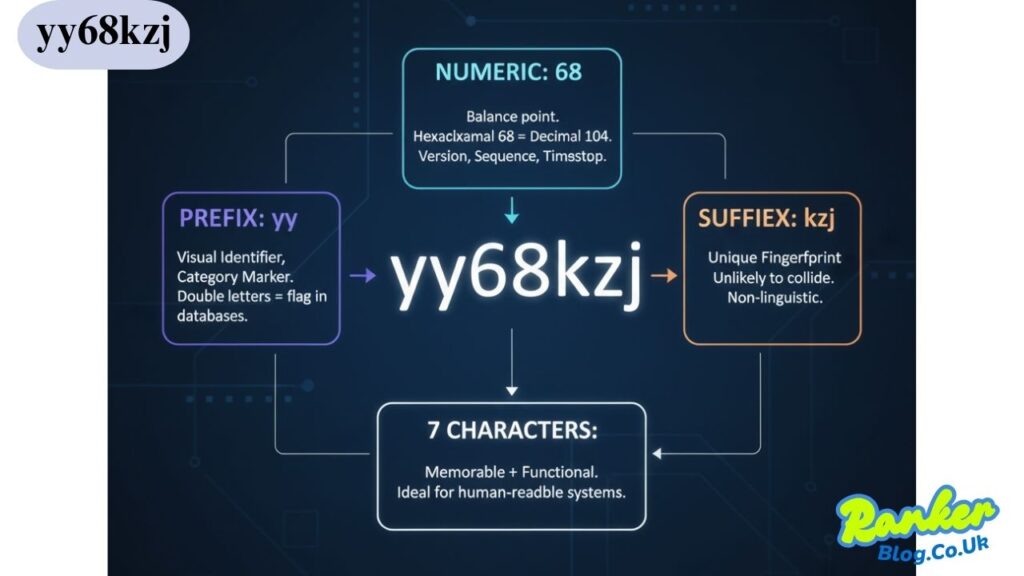
Breaking down yy68kzj reveals fascinating patterns that offer clues about its potential applications. The prefix “yy” could represent a year designation, category marker, or simply a visual identifier that makes the code memorable. Double letters often serve as flags in database systems, signaling specific attributes or classifications.
The numeric component “68” sits perfectly in the middle, creating balance within the sequence. In hexadecimal systems, 68 translates to 104 in decimal notation, though whether this conversion holds significance remains speculative. Numbers within alphanumeric codes frequently represent version numbers, sequence identifiers, or timestamp fragments.
The suffix “kzj” provides the code’s distinctive fingerprint. These three letters create a unique combination that’s unlikely to collide with existing identifiers in most systems. From a linguistic standpoint, “kzj” doesn’t form recognizable words in major languages, reducing the risk of confusion with common terms or commands.
Together, these elements create a code that’s both memorable and functional. The seven-character length strikes an ideal balance—long enough to maintain uniqueness across large datasets, yet short enough for easy manual entry when needed. This sweet spot makes yy68kzj particularly valuable for systems requiring human-readable identifiers.
yy68kzj in the Wild: Real-World Appearances

Despite its mysterious origins, yy68kzj has begun appearing in various digital contexts. Tech forums occasionally reference the code when discussing identifier systems or database architecture. Some developers have adopted it as a placeholder in documentation, appreciating its neutrality and lack of pre-existing associations.
Social media sleuthing reveals sporadic mentions across platforms, though never with enough context to definitively establish its purpose. These breadcrumb trails suggest yy68kzj exists in multiple ecosystems simultaneously—perhaps as different entities sharing the same designation by coincidence, or as a deliberately distributed identifier serving a coordinated purpose.
The code’s appearance in search engine queries indicates growing curiosity. People aren’t just stumbling upon yy68kzj—they’re actively seeking information about it. These search behavior patterns suggest the code is being encountered in contexts that spark questions, whether through software interfaces, documentation, or digital treasure hunts.
Interestingly, yy68kzj hasn’t yet been claimed by major brands or services, leaving it available for innovative applications. This availability represents a rare opportunity in an internet where meaningful short codes have become increasingly scarce.
yy68kzj and the Rise of Digital Identifiers
The emergence of yy68kzj reflects broader trends in how digital systems organize and reference information. As databases expand exponentially, the need for unique, collision-resistant identifiers grows more critical. Traditional sequential numbering systems struggle to scale across distributed networks, creating demand for more sophisticated approaches.
Alphanumeric codes like yy68kzj offer advantages over purely numeric systems. They compress more information into fewer characters while remaining human-readable. This compression matters in contexts where identifiers must fit within character limits or be communicated verbally without confusion.
The format also demonstrates resilience against common data entry errors. The mixture of letters and numbers creates natural checkpoints that help users recognize mistakes. If someone accidentally types “yy68kjz” instead of yy68kzj, the error becomes immediately apparent to anyone familiar with the correct sequence.
Modern API development, blockchain technology, and distributed computing all rely heavily on such identifiers. As these technologies mature, codes like yy68kzj may become templates for next-generation identification systems that balance machine efficiency with human usability.
SEO Power: Why yy68kzj is a Low-Competition Goldmine
This guide goes deep into the rabbit hole of yy68kzj, peeling back its layers, decoding its digital DNA, and exploring why it could be more significant than you might think. From an SEO perspective, the keyword represents a fascinating opportunity for early adopters willing to stake their claim in uncharted territory.
Search competition for yy68kzj remains virtually nonexistent. Major content platforms haven’t saturated this keyword space, leaving room for authoritative content to dominate search results quickly. For digital marketers and content creators, this represents a rare blank canvas where strategic positioning can yield disproportionate visibility.
The specificity of yy68kzj makes it ideal for targeting niche audiences. Anyone searching for this exact term likely has specific intent—whether researching a code they encountered, investigating a technical reference, or exploring cryptographic patterns. This high-intent traffic converts better than broad, competitive keywords that attract casual browsers.
Long-tail opportunities surrounding yy68kzj also remain untapped. Related searches, question-based queries, and contextual variations all present pathways for comprehensive content strategies. Building authority around this keyword now could establish lasting search dominance as interest grows.
Creative Applications for yy68kzj
The versatility of yy68kzj extends far beyond theoretical discussion. Developers can implement it as a project codename, creating internal references that don’t reveal project details to outside observers. This operational security benefit appeals to startups working on innovative products before public launch.
Artists and creators might adopt yy68kzj as a signature element, embedding it in digital artwork, music metadata, or literary works as an Easter egg for observant fans. Such hidden references build community engagement and reward close attention with discoverable secrets.
The code also serves educational purposes. Teaching database design, cryptography basics, or information architecture becomes more engaging when students work with memorable real-world examples like yy68kzj rather than abstract placeholders.
Gamification represents another frontier. Puzzle designers could incorporate yy68kzj into alternate reality games or scavenger hunts, using its mystery as a narrative device that drives player exploration. The code’s existing obscurity provides built-in intrigue without requiring elaborate backstory invention.
How to Create Your Own yy68kzj-Based System
Understanding the structure behind yy68kzj enables the creation of similar identification systems tailored to specific needs. Start by determining the optimal character length for your use case. Seven characters work well for yy68kzj, but your application might benefit from longer or shorter sequences.
Decide on character composition rules. Will your system use only lowercase letters, or include uppercase and special characters? Each decision affects both collision probability and user experience. The lowercase-only approach of yy68kzj maximizes readability and reduces case-sensitivity issues.
Implement validation logic to ensure generated codes meet your structural requirements. Regular expressions can verify that identifiers follow the intended pattern before entering databases. This front-end validation prevents malformed entries that could cause downstream problems.
Consider how codes will be assigned and managed. Will they generate sequentially, randomly, or through deterministic algorithms? Each method carries trade-offs between predictability, distribution, and generation speed. The apparent randomness of yy68kzj suggests algorithmic generation rather than sequential assignment.
Document your system thoroughly. Future developers will need clear guidelines about code structure, generation methods, and intended usage. Comprehensive documentation transforms a clever identifier system into a maintainable long-term solution.
Future-Proofing with yy68kzj
As digital ecosystems evolve, identifiers like yy68kzj gain importance. The transition toward decentralized systems, where no central authority controls naming conventions, increases demand for self-describing, collision-resistant codes. Early adoption of robust identification strategies positions projects for sustainable growth.
The seven-character format provides expansion room. Should systems need to scale beyond current capacity, adding prefixes or suffixes to yy68kzj-style codes maintains consistency while enabling growth. This extensibility proves crucial for projects that start small but aspire to scale.
Cross-platform compatibility matters increasingly as services integrate across devices and ecosystems. Codes structured like yy68kzj work universally—they don’t depend on specific character sets, don’t trigger unexpected parsing in various programming languages, and display consistently across interfaces.
Archival considerations also favor well-designed identifiers. Digital historians decades from now will appreciate codes that remain interpretable without extensive context. The clean structure of yy68kzj ages better than systems relying on contemporary assumptions that may not hold true long-term.
Final Thoughts
The journey through yy68kzj reveals how seemingly simple alphanumeric sequences carry unexpected depth. Whether the code represents a deliberate creation or a happy accident, its structure and potential applications deserve recognition. As digital infrastructure grows more complex, understanding identifier design becomes essential knowledge for developers, marketers, and digital strategists alike.
What makes yy68kzj particularly intriguing is its accessibility. Unlike proprietary systems requiring licenses or permissions, this code exists in the public domain, free for anyone to explore, adopt, or reimagine. That openness invites experimentation and innovation in ways that closed systems cannot.
The mystery surrounding yy68kzj need not be completely solved to extract value from studying it. Sometimes the questions prove more valuable than answers, sparking creativity and driving exploration into uncharted digital territories. Whether you encounter this code in technical documentation, adopt it for your own projects, or simply appreciate its elegant simplicity, yy68kzj stands as a testament to the hidden complexity underlying our digital world.
Also Read: The Role of Relatability in Creator-Driven Engagement

